OpenClaw Deep Dive: Architecture, Agent Loop, and What Makes It Tick
2026-02-07 · CHATTERgo Team · AI Agents, Open Source, Architecture, Technical Deep Dive, OpenClaw
In our previous post, we introduced OpenClaw — the viral open-source AI agent (formerly Clawdbot) that crossed 145,000 GitHub stars in a week. That post covered the what and why. This post goes deeper: we analyzed the actual source code (version 2026.1.30) to understand how it works — and specifically, how OpenClaw builds on top of Pi.
What we found is a remarkably well-engineered system with ideas that challenge how most of the industry thinks about building AI agents.
The Pi Foundation: Four Packages, One Philosophy
At the heart of OpenClaw is Pi — a minimal coding agent created by Mario Zechner. As Armin Ronacher wrote in his analysis, Pi is interesting for two reasons:
- It has a tiny core. Pi has the shortest system prompt of any agent and only four tools:
Read,Write,Edit,Bash. - It makes up for its tiny core with an extension system that allows extensions to persist state into sessions.
This is a deliberate architectural decision, not a limitation. Pi's philosophy: if you want the agent to do something new, you ask the agent to extend itself. No MCP protocol, no skill marketplace downloads — the agent writes its own code.
As Ronacher puts it:
"This is not a lazy omission. This is from the philosophy of how Pi works. Pi's entire idea is that if you want the agent to do something that it doesn't do yet, you don't go and download an extension or a skill or something like this. You ask the agent to extend itself. It celebrates the idea of code writing and running code."
How OpenClaw Consumes Pi
Looking at the actual package.json, OpenClaw depends on four Pi packages (all at v0.51.0):
| Package | Role |
|---|---|
@mariozechner/pi-agent-core |
Core types: AgentMessage, AgentTool, AgentEvent, StreamFn |
@mariozechner/pi-ai |
LLM abstraction: Model<Api>, complete(), streamSimple(), OAuthCredentials |
@mariozechner/pi-coding-agent |
Session management: SessionManager, createAgentSession(), Skill, ExtensionContext, tool factories (createReadTool, createWriteTool, createEditTool, codingTools) |
@mariozechner/pi-tui |
Terminal UI: TUI, Component, SlashCommand, interactive widgets |
OpenClaw doesn't fork Pi — it wraps it. The Pi agent core provides the fundamental agent loop, tool system, and session management. OpenClaw adds everything else on top: the gateway, channels, additional tools, memory, browser automation, and the subagent system.
flowchart TB
subgraph PI["Pi Packages (v0.51.0)"]
direction TB
PAC["pi-agent-core<br/>AgentMessage, AgentTool, AgentEvent"]
PAI["pi-ai<br/>Model, complete(), stream(), OAuth"]
PCA["pi-coding-agent<br/>SessionManager, AgentSession,<br/>Read/Write/Edit/Bash tools,<br/>Skills, Extensions"]
PTU["pi-tui<br/>TUI, Components, SlashCommands"]
end
subgraph OC["OpenClaw Layer"]
direction TB
EMB["Pi Embedded Runner<br/>(wraps Pi's agent loop)"]
TW["Tool Wrappers<br/>(extends Pi's 4 tools)"]
OT["20+ Additional Tools<br/>browser, message, exec,<br/>web_search, image, cron,<br/>sessions_spawn, memory..."]
TP["8-Layer Tool Policy<br/>profile → provider → global →<br/>agent → group → sandbox →<br/>subagent"]
EXT["Pi Extensions<br/>Context Pruning,<br/>Compaction Safeguard"]
end
subgraph INFRA["OpenClaw Infrastructure"]
GW["Gateway + Channels"]
MEM["Memory + Vector Search"]
SUB["Subagent Registry"]
SEC["Security + Sandbox"]
ACP["Agent Communication<br/>Protocol (ACP)"]
end
PI --> OC
OC --> INFRA
How OpenClaw Wraps Pi's Tools
OpenClaw doesn't just use Pi's four core tools as-is. It wraps each one with production-hardening layers, visible in src/agents/pi-tools.ts:
Read → createOpenClawReadTool: Wraps Pi's createReadTool() with MIME detection (validates image types via file magic), image sanitization (removes oversized images before sending to providers), and Claude Code compatibility (file_path alias for path).
Write → sandboxed wrapper: Wraps Pi's createWriteTool() with path guards when sandbox mode is active, preventing file writes outside the sandbox root.
Edit → sandboxed wrapper: Wraps Pi's createEditTool() with parameter normalization (old_string/new_string → oldText/newText for Claude compatibility) and sandbox path guards.
Bash → replaced entirely: Pi's bash tool is replaced with OpenClaw's exec tool — a significantly more sophisticated execution engine supporting Docker sandbox execution, background process management (via a separate process tool), security policies (ask/deny/allow per command), elevated mode, timeout handling, approval workflows for long-running processes, and scope-based process tracking.
Beyond the core four, OpenClaw adds 20+ additional tools:
| Category | Tools |
|---|---|
| Messaging | message, sessions_send, sessions_spawn, sessions_list, sessions_history |
| Browser | browser (13 sub-actions: navigate, snapshot, act, tabs, console, pdf...) |
| Web | web_search, web_fetch |
| Media | image (vision analysis), tts (text-to-speech) |
| Infrastructure | gateway, nodes, cron, canvas, memory |
| Channel-specific | discord_actions, slack_actions, telegram_actions, whatsapp_actions |
| Code | apply_patch (OpenAI Codex-specific), process (background jobs) |
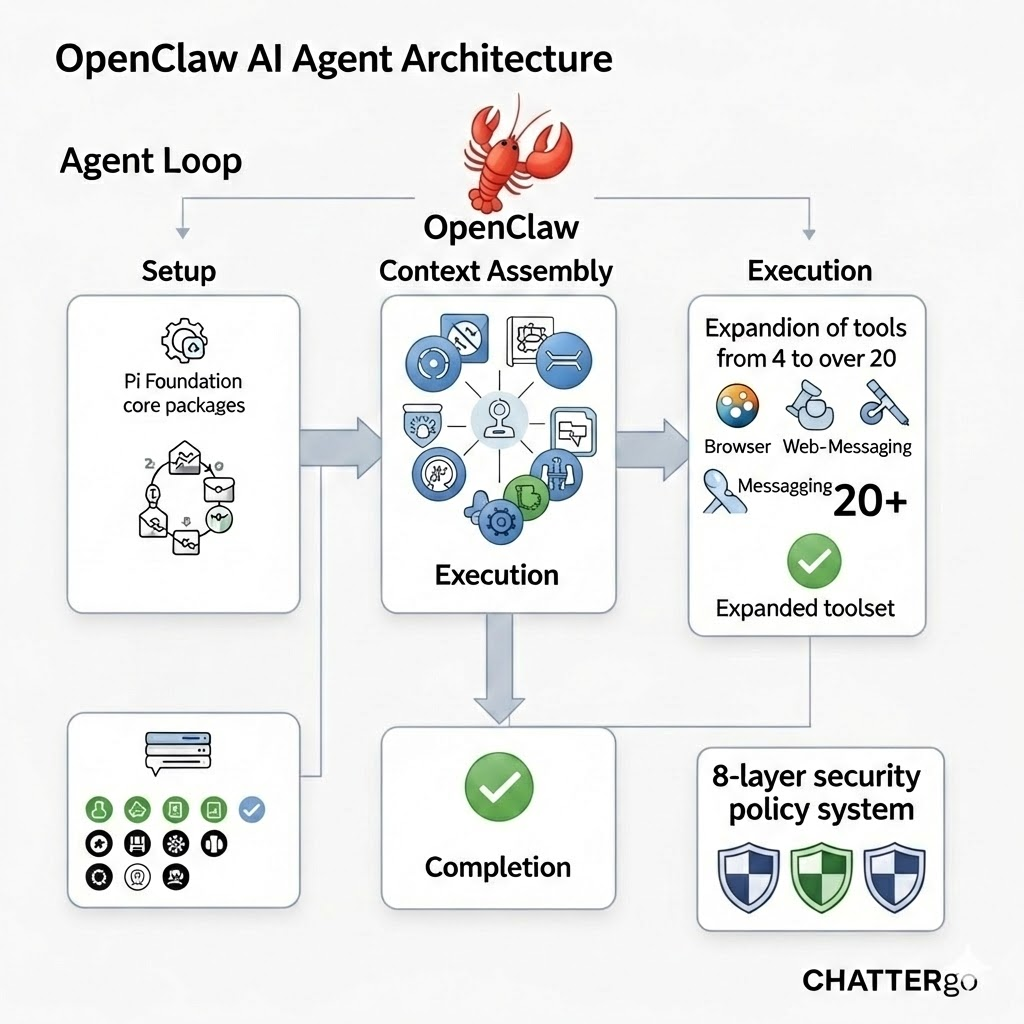
The Embedded Runner: OpenClaw's Agent Loop Wrapper
The most important integration point is the Pi Embedded Runner (src/agents/pi-embedded-runner/). This is how OpenClaw wraps Pi's agent loop for multi-channel use:
flowchart TB
ENTRY["Entry Points<br/>Gateway RPC / CLI / Cron / Webhook"]
subgraph P1["Phase 1: Setup"]
WS["Resolve Workspace + Sandbox"]
TOOLS["Build OpenClaw Tools<br/>(Pi's 4 + 20+ extras)"]
SM["Open SessionManager<br/>(Pi JSONL store)"]
SETTINGS["Load SettingsManager<br/>(Pi workspace config)"]
AGENT["createAgentSession()<br/>(Pi factory)"]
end
subgraph P2["Phase 2: Context Assembly"]
SYS["Build System Prompt<br/>Base + Tools + Skills +<br/>SOUL.md + USER.md +<br/>AGENTS.md + HEARTBEAT.md"]
MODEL["Resolve Model + Auth<br/>(Pi ModelRegistry +<br/>OpenClaw AuthStorage)"]
HIST["Load Full History<br/>(Pi SessionManager)"]
SAN["Sanitize History<br/>(Anthropic/Gemini turn ordering)"]
IMG["Auto-inject Images<br/>(vision model detection)"]
PRUNE["Context Pruning Extension<br/>(soft trim / hard clear)"]
end
subgraph P3["Phase 3: Execution"]
PROMPT["session.prompt()<br/>(Pi agent loop)"]
STREAM["subscribeEmbeddedPiSession()<br/>(OpenClaw stream wrapper)"]
POLICY["8-Layer Tool Policy<br/>Check before each tool call"]
end
subgraph P4["Phase 4: Completion"]
COMP["Compaction if Triggered<br/>(Pi + Safeguard Extension)"]
PERSIST["Persist to JSONL"]
REPLY["Shape + Send Reply<br/>to Channel"]
CLEANUP["Dispose Session +<br/>Release Locks"]
end
ENTRY --> P1
P1 --> P2
P2 --> P3
P3 -->|"Tool calls loop<br/>back through Pi"| P3
P3 --> P4
What the Embedded Runner Does
- Workspace setup: Resolves the agent's workspace directory, sandbox configuration, and skills snapshot
- Tool creation: Calls
createOpenClawCodingTools()— which takes Pi'scodingToolsarray and replaces/wraps each tool, then adds 20+ OpenClaw-specific tools - Session initialization: Opens Pi's
SessionManager(JSONL transcript), createsSettingsManager, then calls Pi'screateAgentSession()factory - System prompt override: Assembles the full system prompt from base prompt + tool summaries + skills + bootstrap files (SOUL.md, USER.md, etc.) + runtime info
- History sanitization: Validates and fixes provider-specific turn ordering (Anthropic requires alternating user/assistant turns; Gemini requires a user turn at the start)
- Prompt execution: Calls
session.prompt()— this is Pi's actual agent loop running - Stream subscription:
subscribeEmbeddedPiSession()wraps Pi's stream with OpenClaw-specific handling: block replies, reasoning extraction, partial reply callbacks to the gateway - Compaction: If triggered, runs Pi's
session.compact()with the Compaction Safeguard extension ensuring it doesn't consume too much context
The 8-Layer Tool Policy System
One of the most sophisticated pieces of OpenClaw's architecture is its tool policy system. Before any tool executes, it passes through eight layers of allow/deny filters:
- Profile policy (
tools.profile) — named policy presets - Provider profile (
tools.byProvider.profile) — per-LLM-provider overrides - Global allowlist (
tools.allow) — instance-wide restrictions - Provider allowlist (
tools.byProvider.allow) — per-provider global restrictions - Agent-specific (
agents.{id}.tools.allow) — per-agent restrictions - Group policy — channel-level restrictions (e.g., disable
execin Discord servers) - Sandbox policy — Docker sandbox restrictions
- Subagent policy — restrictions for spawned sub-agents
This means a browser tool allowed in your personal WhatsApp session can be denied in a Discord group chat, while a sandboxed subagent might have a different restriction set entirely. Each layer narrows the available tools — the most restrictive combination wins.
Pi Extensions: Context Pruning and Compaction Safeguard
OpenClaw ships two custom Pi extensions that hook into Pi's lifecycle events:
Context Pruning Extension
Located in src/agents/pi-extensions/context-pruning/, this extension intercepts the pre-LLM-call phase and prunes old tool results when the context window is tight:
- Soft trim: Truncates large tool results, keeping head + tail
- Hard clear: Replaces very old tool results with placeholders
- Protection: Never prunes before the first user message (protects bootstrap reads), and respects a
keepLastAssistantssetting - Trigger: Only activates when the Anthropic cache TTL expires (default: 5 minutes), reducing unnecessary cache write costs
Compaction Safeguard Extension
Located in src/agents/pi-extensions/compaction-safeguard.ts, this intercepts Pi's session_before_compact event:
- Prevents compaction from consuming too much context
- Summarizes dropped messages separately
- Tracks file operations (read/modified files) and includes them in summaries
- Includes tool failure summaries
These extensions demonstrate Pi's architecture at work: they're loaded as file paths that Pi discovers at runtime, and they persist state via Pi's SessionManager.
Subagent System
OpenClaw adds a subagent orchestration layer (src/agents/subagent-registry.ts) on top of Pi:
- Spawning: The
sessions_spawntool creates subagent sessions with their own workspace and tool set - Registry: Tracks subagent runs in memory + disk
- Lifecycle: Listens to Pi agent events for start/complete/error
- Cleanup: Configurable policies —
deleteorkeepfinished subagent data - Announcements: Notifies the parent agent when a subagent completes
- Cross-process: Uses gateway RPC for waiting on subagents across processes
This is how OpenClaw agents can delegate tasks: "Research this topic" spawns a research subagent, "Draft a response" spawns a writing subagent — all coordinated by the parent.
Agent Communication Protocol (ACP)
OpenClaw implements the Agent Communication Protocol (src/acp/) — an emerging standard for agent-to-agent communication:
- Server: Implements
AgentSideConnectionfrom@agentclientprotocol/sdk - Translator: Bridges between ACP and OpenClaw's gateway protocol
- Session mapping: Maps ACP sessions to OpenClaw session keys
- Event mapping: Converts gateway lifecycle events to ACP events
This allows external ACP-compatible clients to control OpenClaw agents via stdio (NDJSON), opening the door for interoperability with other agent frameworks.
Memory: Vector Search + Semantic Files
OpenClaw's memory system (src/memory/) goes beyond simple file storage:
- Vector embeddings: Supports OpenAI, Gemini, and local node-llama-cpp embedding providers
- SQLite-vec: Local vector storage using SQLite with vector extensions
- Hybrid search: Combines vector similarity search with keyword matching
- Auto-indexing: Automatically indexes session transcripts,
MEMORY.md, and daily notes - Deduplication: Prevents duplicate entries across re-indexes
The memory tool lets the agent search across its own history semantically — "What did I discuss about the API project last Tuesday?" — without needing the full history in context.
Security scoping remains critical:
- Main session (direct chat with the owner): Can read/write
MEMORY.mdand access vector search - Group sessions: Cannot access
MEMORY.mdor personal memory — preventing data leakage
Browser Automation: Playwright + AI Snapshots
OpenClaw implements a sophisticated browser control system (725 lines in browser-tool.ts) built on Playwright with Chrome DevTools Protocol (CDP) integration.
flowchart LR
subgraph PROFILES["Browser Profiles"]
OC["openclaw<br/>Managed Playwright"]
CE["chrome extension<br/>Extension Relay"]
SB["sandbox<br/>Docker Container"]
RM["remote<br/>Browserless.io"]
end
subgraph TOOLS["13 Browser Actions"]
NAV["navigate"]
SNAP["snapshot"]
SCRN["screenshot"]
ACT["act (click/type/drag)"]
TABS["tabs / open / focus / close"]
CON["console"]
PDF["pdf"]
end
REQ["Agent Tool Call"] --> PROF["Profile Selection"]
PROF --> PROFILES
PROFILES --> PW["Playwright Connection"]
PW --> TOOLS
TOOLS --> RES["Role References<br/>e1, e2, e3..."]
RES -->|"Used in future actions"| REQ
The Vision System: No External Libraries
OpenClaw does not use external vision libraries (tesseract, pixelmatch, etc.) for understanding web pages. Instead, it leverages Playwright's internal _snapshotForAI method — an accessibility tree API that generates stable, role-based element references.
The agent references elements by their stable refs: click e7, type e4 "user@example.com". This is more reliable than pixel-based approaches because role references survive page layout changes, animations, and responsive breakpoints.
Multi-Profile Architecture
- openclaw — Playwright-managed browser with its own user data directory. Complete isolation from your personal browser.
- chrome extension — Connects to your actual Chrome browser via a local extension relay. Useful when you need access to logged-in sessions.
- sandbox — Docker containerized browser. Full isolation for untrusted sites.
- remote — Browserless.io or similar remote CDP endpoint. For server-side automation.
Skills: Self-Extending with a Safety Net
Skills are markdown files (SKILL.md) with YAML frontmatter, loaded from multiple sources in priority order:
- Workspace skills (
./skills/) — highest priority - Managed skills (
~/.openclaw/skills/) - Bundled skills (npm package)
- Extra directories (config)
- Plugin skill directories
- ClawHub (clawhub.com) — public registry
Skills include a gating system that checks OS compatibility, required binaries, environment variables, and config values before loading. They can also be converted to slash commands (/skillname) with automatic deduplication.
But the Pi philosophy remains: while you can download skills, the encouraged pattern is to have your agent write its own. As Ronacher describes:
"My agent has quite a few skills and crucially I throw skills away if I don't need them. I have a skill to help the agent craft the commit messages and commit behavior I want, and how to update changelogs."
Security Model
OpenClaw's security is layered across inbound, execution, and data boundaries:
- Inbound: DM pairing (unknown senders get a verification code), explicit allowlists, group mention gating
- Execution: Docker sandboxing for non-main sessions, the 8-layer tool policy system, per-session elevated mode toggle
- Data: Local-only storage, memory scoping (main vs. group), credential storage in
~/.openclaw/credentials/ - Network: Gateway WebSocket on loopback only (
127.0.0.1:18789), token-based authentication
Three permission levels: non-main (most restricted), main (normal), elevated (explicitly toggled for sensitive operations).
What This Means for AI Agent Architecture
Our source code analysis revealed several architectural patterns worth noting:
1. Wrap, don't fork. OpenClaw depends on Pi as npm packages, wrapping its tools and session management rather than forking the codebase. This means Pi improvements automatically flow downstream.
2. The 4-to-24+ tool expansion pattern. Pi starts with 4 tools. OpenClaw wraps those 4 and adds 20+ more — but all pass through Pi's unified AgentTool interface. The agent loop doesn't care how many tools exist; it just executes what the LLM selects.
3. Multi-layer policy systems are essential for multi-tenant agents. When one agent serves WhatsApp DMs, Discord servers, and sandboxed subagents simultaneously, you need composable security policies — not a single allow/deny list.
4. Extensions > plugins for agent-internal concerns. Pi's extension system (lifecycle hooks + state persistence) is better suited for agent-internal concerns (context management, compaction) than a plugin system, because extensions can intercept the agent loop itself.
5. Full history with smart eviction. OpenClaw passes complete conversation history to the LLM, using compaction (persistent summarization) and pruning (transient trimming) to manage costs — preserving nuance that aggressive summarization would lose.
How This Relates to CHATTERgo
At CHATTERgo, we share philosophical alignment with OpenClaw — particularly the emphasis on autonomous, tool-using agents over pre-scripted workflows. Our AI agents also:
- Reason dynamically about customer queries rather than following flowcharts
- Use tools (catalog search, order lookup, knowledge base) selected at runtime
- Maintain conversation context across sessions
- Extend capabilities through custom tools, APIs, and MCPs
The key difference is our domain focus. OpenClaw is a general-purpose personal agent that runs on your hardware. CHATTERgo is a purpose-built eCommerce agent that runs as a managed service — optimized for product recommendations, customer support, and multi-language commerce operations.
Both approaches point to the same future: AI that does things, not just talks about them.
Sources
- OpenClaw source code (v2026.1.30): github.com/openclaw/openclaw
- OpenClaw Documentation: docs.openclaw.ai
- OpenClaw Website: openclaw.ai
- ClawHub Skills Registry: clawhub.com
- Armin Ronacher, "Pi: The Minimal Agent Within OpenClaw," January 31, 2026: lucumr.pocoo.org/2026/1/31/pi
- CHATTERgo Code Analysis — OpenClaw Architecture Deep Dive (v2026.1.30): app.chattergo.com/apps/public/doc/c2758da9
- CHATTERgo Code Analysis — OpenClaw Browser Control System: app.chattergo.com/apps/public/doc/5965a85b
